Configuring Windows to forward logs to a SIEM.
For this task you are going to setup windows event log forwarding into a SIEM.
Refer to previous lab activities on how to do this.
- Login to the Windows 10 system.
- Open the Splunk link on the Desktop. Login with admin/changeme
- Configure Splunk to receive data.
- Install the Splunk Universal Forwarder.
- Install and Configure Sysmon.
- Add Sysmon to the universal forwarder.
- Restart the universal forwarder or reboot the Windows 10 system.
- Run a search query in Splunk to verify all logs have been forwarded from Windows 10.
- Install the universal forwarder on the Window 7 system.
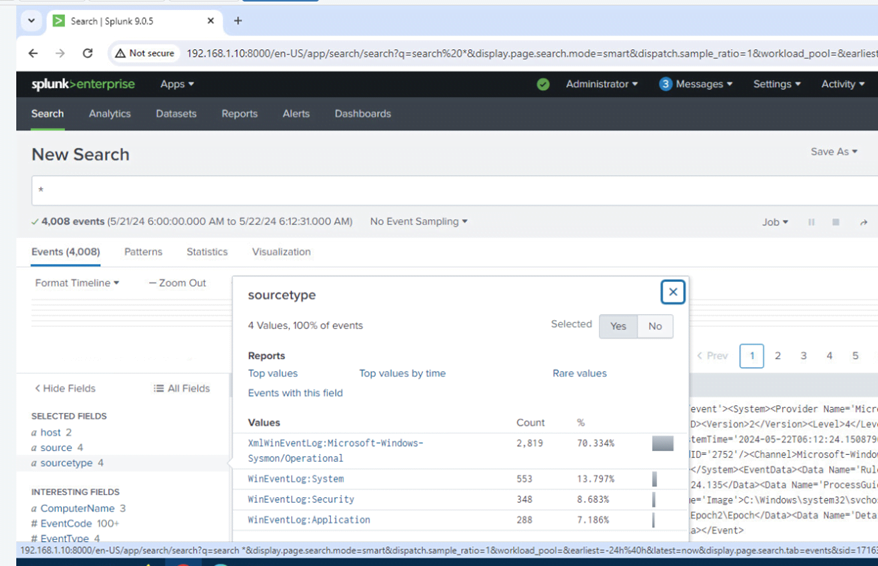
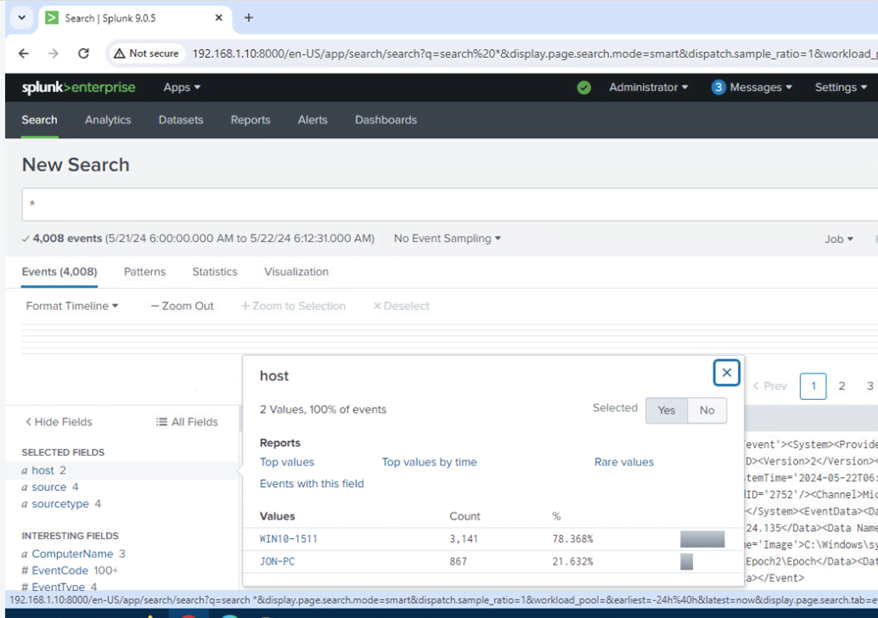
Take a screenshot of the new search query showing the event logs are being forwarded (screenshot should show 2 hosts and 4 sourcetypes) and paste it over the image in the table below.