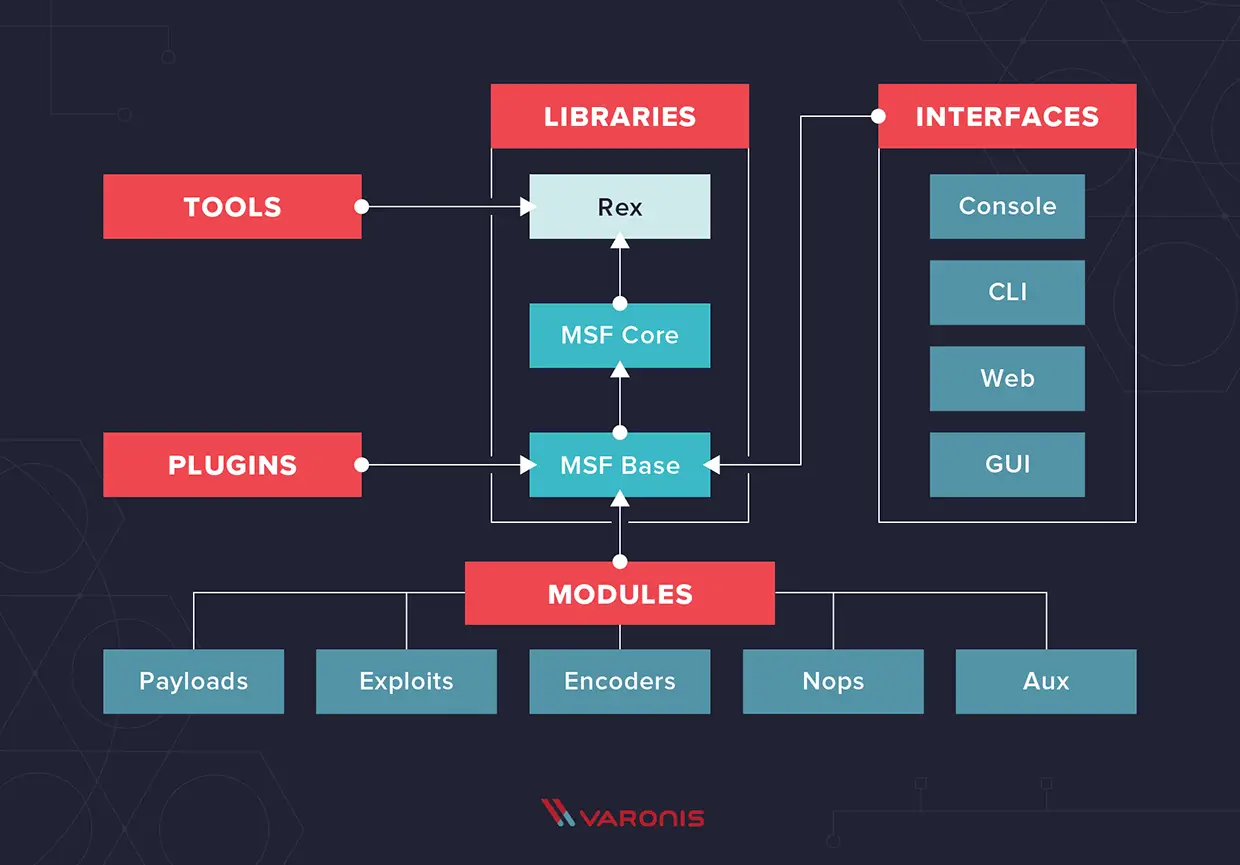
5. Auxiliary Modules
Description:
Auxiliary modules are used for scanning, fuzzing, and performing other actions that don’t necessarily involve exploiting a vulnerability. These can be used for tasks like vulnerability scanning or enumeration.
Examples:
- Use an Auxiliary Module:
- use auxiliary/scanner/smb/smb_version
- Use an Auxiliary Module:
Explanation: Uses the SMB version scanner to identify the version of SMB running on a target.
